- PRODUCTS
- Security Platform
- BioStar X | On-Prem SecurityNEW
- BioStar Air | Cloud Security
- BioStar 2
- Access Control
- Access Control Unit
- Biometric Readers
- RFID Readers
- Mobile Credential
- Peripherals
- Wireless Door Locks
- SOLUTIONS
- SUPPORT
- ABOUT
- device_hubHUB
What is Access Control
Access control is a form of physical security that manages who has access to an area at any given time. Access control systems restrict access to authorized users and provide a means to keep track of who enters and leaves secured areas.
Access control plays a critical role in the safety, security and day-to-day operations of businesses and organizations worldwide.
From ensuring permitted entrances into buildings, to physically safeguarding sensitive information, access control systems add a necessary layer of safety for the protection of employees, assets, and facilities.

Electronic access control systems are widely used across industries, and include the implementation of electrified doors, turnstiles, guards, and gates to keep an area secure. For example, in a door entry system in an access-controlled building, authorized persons use credentials (physical, digital via a mobile device, or biometric) to make unlock requests at readers, which send information to an Access Control Unit (ACU), also known as an access control panel or a controller. The ACU then triggers the electrified door hardware to unlock if authorized. This is also commonly referred to as a door access control system or door entry system.
With many options of access control systems on the market, spanning across physical and digital protection of assets, evaluating solutions and their components can quickly become a massive undertaking.
Why Access Control Systems
Access control security measures are designed to protect buildings and to safeguard the equipment inside. In short, they keep unwanted people out, and give access to authorized individuals. While network and cybersecurity are important, preventing physical security breaches and threats is key to keeping technology and data safe, as well as any staff or visitors who have access to the building. Without physical security plans in place, offices or buildings are left open to criminal activity, and liable for types of physical security threats including theft, vandalism, fraud, and even accidents.
In today’s infrastructure, we often think of physical access control as locks, gates, and guards. While these are effective, there are many additional and often forgotten layers to physical security that help protect all assets. For example, a door access control system that uses keyless entry protects people and assets while keeping track of who enters, when and where they enter, and how long they stay in the building. When it comes to access control systems, the most common credentials are keycards and fob entry systems and mobile access devices. Some access control systems allow you to use multiple types of credentials on the same system, too. A comprehensive physical security plan combines both technology and specialized hardware, and should include countermeasures against intrusion.

Types of Access Control
At its core, access control is a means of securing something from those that shouldn’t have access to it. There are many technologies that satisfy the need to secure people, assets, and information, but at its core, there are two types of access control solutions: physical and logical.
Physical access control, as its name implies, provides organizations with a means of securing their physical spaces. This security can range from managing access to sensitive areas like a server room, the pharmacy in a hospital, or the entire building itself. In this form of door access control, users gain entry with credentialed access, including key cards, fobs, and smartphones.
Logical access control implement protections for digital assets, including access to programs, databases, and other forms of data that need protection from unauthorized visitors.
While the primary focus here is physical access control, there is undoubtedly a growing intersection between physical and logical access control. From role-based access of user management software to integrations with enterprise software for automating rules around credentials, the increasing combination of the two only helps make organizations more safe and secure.
Physical access control systems require a form of unique identification to authenticate and authorize an individual asking for access. Most access control security systems use one of the following methods for identification

Key cards, fobs and badges
With a key card entry system, authorized users swipe, tap, or wave their card at a reader to gain entry. Key cards and fobs are supported on most legacy access control systems, but can be more difficult and costly to manage. Plus, they require in-person administration.

Mobile credentials
Quickly becoming the preferred method for many companies, this credential type relies on a user’s smartphone for entry. Mobile credentials offer better security, as all credential information is stored on the phone, and people are less likely to lose or forget their phone than an ID badge or a key fob. Even if a phone is misplaced, most mobile phones have password protection or lockdown capabilities to prevent others from gaining access. Mobile credentials also are easier to manage; admins can instantly add or revoke permissions via user management software without any face-to-face interaction.

Biometrics
This more advanced security measure requires a user to authenticate with their fingerprint, iris scan, or facial authentication to gain entry. Fingerprint recognition is the most widespread biometrics authentication for access control, but over the last five years the accuracy of facial authentication has improved to achieve parity. Facial Authentication has seen increased use during the COVID-19 pandemic, replacing touch-based technology as organizations looked to minimize risk and offer employees and visitors a healthier environment.
Access Control in the age of COVID
The trend today is to include on an access control list a system that helps prevent the spread of infectious diseases. One straightforward way organizations address the pandemic is by adopting touchless biometric authentication like face or iris recognition. Historically, biometric credential was used as part of multi-factor authentication for security reasons, but as accuracy and reliability improved, it has come to replace single-factor traditional authentication methods like RFID card and PIN. Facial Authentication has especially gained traction in recent years, peaking with the outbreak of COVID-19, replacing touch-based technology as organizations looked to minimize risk and offer employees and visitors a healthier environment.

Access control systems have also come to include features that reduce physical contact between people. Remote user enrollment and management features lets admins grant and revoke access rights without having to meet employees and visitors in person. Occupancy limit feature that only permits a certain number of people in confined space is another popular feature. Advanced tracking feature also enables contact tracing, helping prevent further spread of the disease.
Building and implementing a COVID-19 physical security control plan may seem daunting, but with the right technology investments now, building and assets will be better protected well into the future. Because common touch points are a main concern for many tenants and employees upgrading to a touchless access control system is a great first step.
How to Choose an Access Control System
When it comes to choosing an access control system, there are many factors to consider; ranging from how the system is implemented, as well as how users look to manage and access their access control system. Consider the following factors when planning and choosing a system:
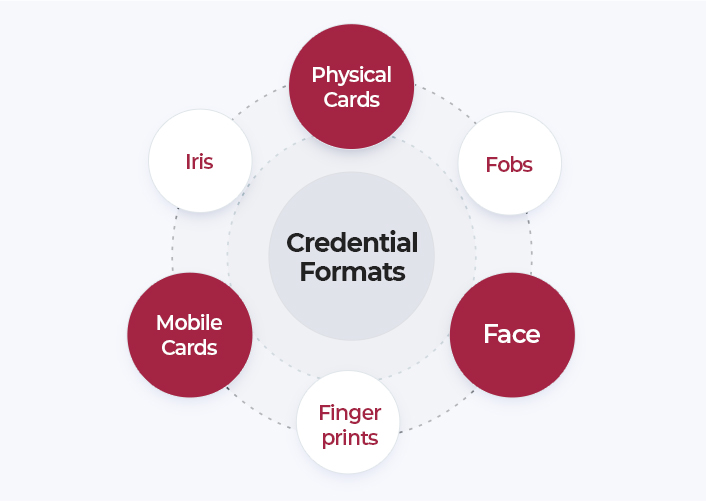
Credential Formats
The first decision organizations must consider is the type of credentials used to secure access points. As mentioned earlier, there are many credential formats, ranging from physical cards and fobs, to biometric datalike fingerprints, face or iris, to mobile access cards that store credentials in smartphones.
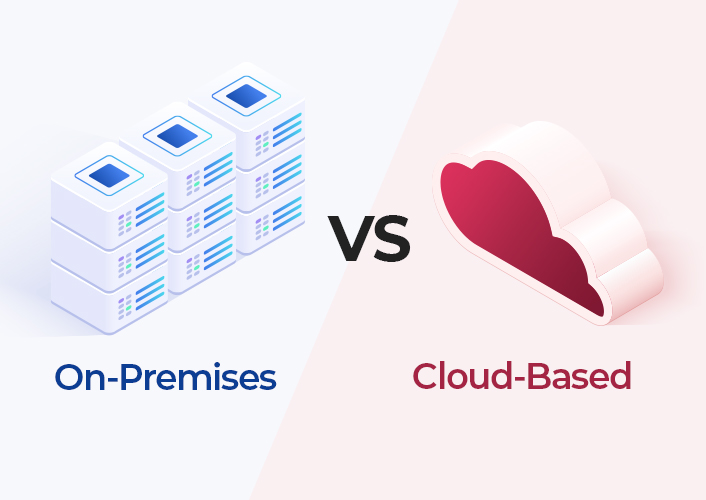
On-Premises vs. Cloud-Based
The implementation and management of a door access control system starts with choosing between an on-premise access control system and a cloud-based solution. When choosing between the two, take into account how the organization manages, scales, and operates day-to-day building access.
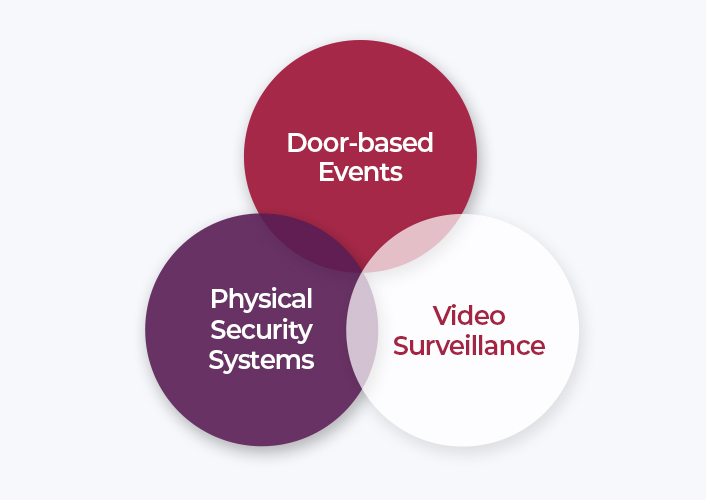
Integrations
In addition to knowing door-based events, an access control system can be more useful when integrated with other physical security systems such as video surveillance.
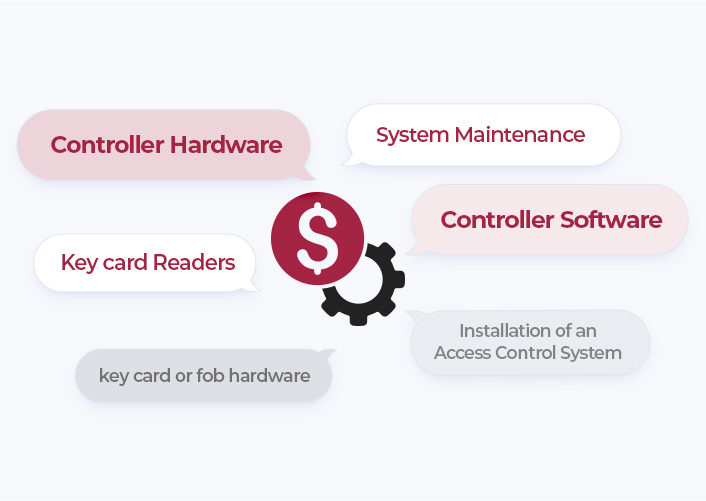
Price
There are many factors that play a part in determining a door access control system price. Door access controller hardware and software may make up the majority of the cost, however, there are other costs associated with things like key card readers, system maintenance, and installation of an access control system plus any associated key card or fob hardware.

Scalability and User Management
From managing users and doors across multiple locations, understanding scalability needs will help determine the right access control system. In addition to knowing how many doors and credentialed users you will need for building access, it is also necessary to consider how systems will communicate with one another when managing multiple access control systems or locations.

Security
In addition to the physical security access control provides, it is essential also to evaluate the additional security considerations. These considerations can range from how door access controllers connect back to the system, as well as how to select the correct form of RFID/proximity cards.
Putting it all Together
A lot has been said about the types of access control systems, devices, topology, and integration. All important points, but perhaps the most important factor of a successful access control implementation is choosing the right access security control vendor. There are many vendors to choose from, but few that offer a comprehensive and robust solution that easily scales as needs grow.
Suprema combines its renowned biometric algorithms with superior engineering to offer an extensive portfolio that includes biometric access control systems, live fingerprint scanners, mobile authentication solutions and embedded fingerprint modules.
Suprema is an innovator in proximity and contactless access control security, providing advanced facial authentication terminals like FaceStation F2, as well as Mobile Access solution.
Suprema’s access control terminals can be integrated with third party platforms or managed on BioStar 2, Suprema’s web-based, open, and integrated security platform with comprehensive functionality. Featuring a modular, flexible framework, the platform provides a customized system depending on system scale, number of users and system structure that was used.

















